Hacking neighbor Wi-Fi in 5 minutes:
100% working methods to find out the password

Below are considered both the general methods of hacking wireless networks, and given instructions or references to them. In addition, recommendations were given to improve the protection of your own home network from possible evil neighbors and other intruders. I hope the article will be useful to all readers. Others recommend to read more about the proposed material and leave your comments.
Hacking methods
Wireless networks integrate a lot of technology. And where there are a lot of technologies - there are a lot of security technologies. And at the bottom of this “duck in the egg” holes in the security system emerge. And for every possible hole there is a method of attack. In this section, I would like to show all possible ways how to hack Wi-Fi and penetrate a wireless network. But which of these options will work, depends entirely on the specific situation. In addition, it may happen that the network is fully protected and can not be cracked at the current time)
The main ways to hack someone else's Wi-Fi: - Unprotected networks.
- Manual password selection.
- Brute force password.
- Selection of WPS code.
- Phishing Password Database.
- Bypass filters.
- Interception "handshake" and its decoding.
- Hacking the router and pulling out an open password.
Briefly try to look at all these methods. I won't go into details much, but if you suddenly have a question, ask it in the comments.
Is it possible to hack?
Is it possible to hack? - Yes, it is possible.
Is it possible to defend completely? - No you can not.
Because The technology is initially open to connect users.
Unprotected network
Usually in our time, all networks are encrypted and protected by a key. Something like the following image:

But still there are access points that are not protected. And you can connect to them completely freely - without a password. An example of such a point - public places, metro.
Recommendation! Always protect your home network with a password.
Manual selection
These first two methods are written simply to show that sometimes to resort to complex technical actions and it is not worth it, because usually everything is in sight, just think a little.
The average user usually sets himself an uncomplicated password - try to imagine what he could enter and guess it. It works great to find out the Wi-Fi password from a friend and neighbor. What if you already know some kind of password of your neighbor? People like to repeat very much, and usually introduce the same thing. Works rarely, but accurately. Especially on old WEP networks, where passwords of less than 8 characters were allowed to enter - “12345” and “QWERTY” were often encountered there.
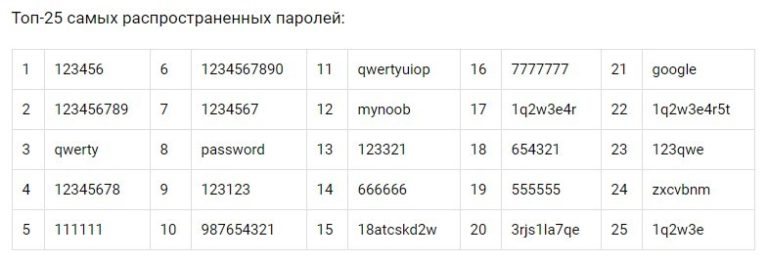
Top 25 most common Wi-Fi passwords Many providers (Rostelecom, ByFly, Yota and others) sometimes use the default passwords on their models. Look for them on the Internet or on our site, suddenly lucky)
Brute forces
There are pluses - old models without attack detection and weak password (WEP) break with a bang. There are minuses - new models can detect you (have to be disguised) and introduce delays in the search, or even a full ban of the attacking machine. Another disadvantage is that modern routers force users to enter complex long passwords that will take years to complete. So it is necessary to look for other methods.
But still try to sort out the network for easy passwords, or if it is WEP, and not WPA / WPA2 definitely worth it. The probability of a hole is always there.
Brutus highlights:
- Programs can use the full brute force option — suitable for the WEP network, or for the router model, which forces you to force complex passwords where a dictionary attack is impossible.
- There is a dictionary attack option - when a file with the most frequently encountered passwords is loaded. There are a lot of these files - in one Kali Linux there are about a couple of dozen of them, and how many go around the network. For me, it is enough to check for basic passwords with a small list - after all, cracking through brute force is no longer an option, but for a basic check and time saving, the simplest list is enough.
- The program works in several threads - i.e. can simultaneously try to sort through many options at once. But it has its own peculiarity: the router itself can reject such attempts, introduce authorization delays or even reboot. Those. with threads you need to play carefully. In any situation - check everything on your hardware, so you will know for sure.
- Some people write about the proxy ... But what kind of proxy is there))) We are connecting through the air) The point is that some programs successfully mask their requests for different devices, which makes it possible to work in multi-threading.
I will give a selection of programs at the end - usually one program like Air-crack (market leader) can do all the actions itself. No need to reinvent the wheel or put 100,500 programs. In the meantime, I want to continue the discussion by way of hacking.
Interception "handshake"
One of the most working methods is to intercept a handshake. What it is? It is also a kind of pure brute, only with a preliminary interception of the cipher and its further attempt to decrypt it. Here is a brief outline:
- You sit quietly on the net.
- The network is breaking.
- Your computer is reconnecting again.
What happens at the time of reconnection: your computer re-sends the password to the router, the router accepts it and, if successful, establishes a connection. In practice, this is absolutely imperceptible - neither a breakaway network, nor a password entry - everything is done automatically by your system.
This process of sending a password can be called “handshake” or “handshake”. But there is a minus in this method - the data is transmitted initially in encrypted form. But with a strong desire, this cipher can still be parsed (even services are available) and password-protected data can be opened. And the time it will take no more than a direct brute force.
That's the whole basis of the method. The Air-crack, which is already familiar to us, is able to remove the handshake, and Hash Cat (the chopper and password generator) can pick up the password. But better watch the video above. This is the very way to calmly break the neighbor's wifi.
That's the whole basis of the method. The Air-crack, which is already familiar to us, is able to remove the handshake, and Hash Cat (the chopper and password generator) can pick up the password. But better watch the video above. This is the very way to calmly break the neighbor's wifi.
WPS code
Some routers have the most useless button - WPS, which allows you to connect devices in a simplified mode. By default, many routers still have WPS enabled. A connection to such a network is carried out only by entering this PIN-code, which consists only of numbers.
The PIN is only 8 digits. Above, I have already spoken about the admissibility of complete enumeration of WEP, and here it is even simpler - only numbers. In addition, a correlation was found, which allows methods to make a selection in pairs - first 4 digits, and then 4 digits. This all speeds up the search, and a point with an open WPS can be broken in a few hours.
Another type of attack is the use of default codes. YES! Some devices from the factory come with the same PIN-code installed. And the proposed programs already know these passwords, so everything can be much easier.
Recommendation: disable WPS in your router! This is basically a useless thing.
Phishing
Another interesting method is to display your page from a web user ... Yes, this can be done without connecting to the network. But the substitution can be seen. The most acceptable option:
- An access point is created with the same name of the network being hacked.
- A good signal and name will force the victim to connect to it sooner or later.
- After logging in, a password is entered that successfully arrives to you.
The method is working, but then you can't do without luck. There are also available software implementation methods, for example, using Wifiphisher .
We will analyze this application in a bit more detail, since interesting attack vector. We will need Kali Linux (yes, guys, all the cool free software for any level of hack is right there, so put it). In the terminal, run:
wifiphisher
Immediately after launching, the program starts searching for the nearest networks (all programs with the network hack do this):
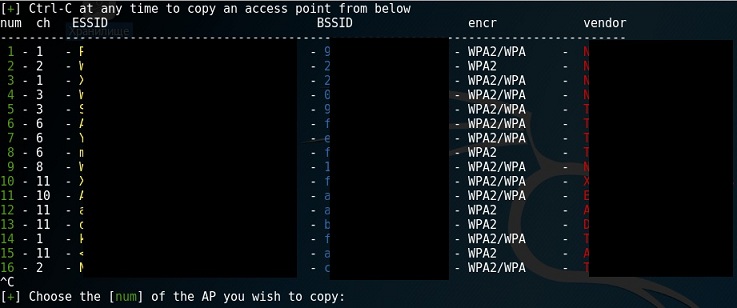
Pay attention to the number of networks. Find the required one in this list and enter its number. Further various attack scenarios will be proposed:
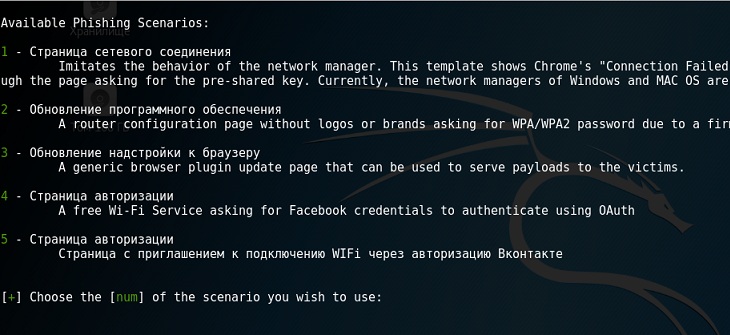
All options are approximately the same, the only difference is that the user of a foreign network will have to - authorization or software update. I recommend to pay attention to the following points:
- Firmware Upgrade Page - you will be asked to upgrade the software of the router itself. It looks interesting and believable, but just need to enter the same key:
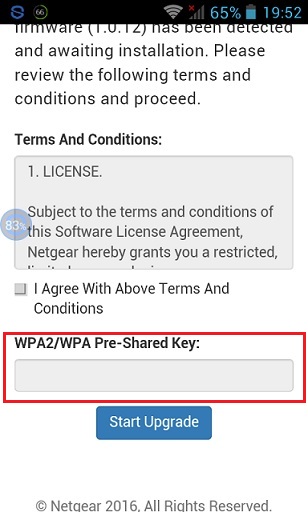
Meanwhile, a password arrives in the console like this:


That's all. The approximate use of all programs comes down to this. I will not dwell on one in detail, otherwise the whole book will turn out. I mark the attack vectors, give hints - and you study each direction on your own. At the end of the article I will give an interesting bonus from professional hackers, for those who want to dive.
Recommendation: Watch your attention if the network to which the device was previously connected automatically without problems requested a password - especially on a third-party page (software update, VKontakte password, etc. - this does not happen). Pay attention to duplicate network at home.
Password Database
There are programs and services that store the password database access points of public places. This is especially true for all cafes in large cities. Want to break a cafe? But why, usually someone has already connected to it, which means there is a possibility that the password has sailed to the bases. An example of such a service application: Wi-Fi Map or Router Scan. And the map will show, and the available points, and it will connect.
Recommendation: make a selection of service and in case of suspicion of hacking, check yourself in these databases. Even easier - every six months, change the password from Wi-Fi.
Hacking router
Sometimes you have the ability to connect via wire to Wi-Fi, or you know the external IP-address from the Internet and can access the router (sometimes you can with high probability determine it and scan).
Then you can try to find a password to enter its control panel. Many people leave it as default admin / admin (login / password). And already in the settings, the Wi-Fi password is stored in clear text.
Filter bypass
Some access points do not allow you, simply because you have an inappropriate ... MAC address. Sometimes it happens. This is not about hacking, but sometimes the whole task of hacking comes down to changing the MAC - for example, when you have successfully connected before, but now it doesn't let you in any way, because administrator or parents banned your device by MAC. The solution is simply to change it.
It happens use:
- Black list. Then you just need to change the address to the one that is not in this list. Universal program - Macchanger.
- White list. Only the devices specified in it are connected. Then, first you need to look at these devices and their addresses (Airodump-ng will do), and after that, they should be adjusted to them by the same mac-changer.
Network security
I will highlight some of the problems that are worth paying attention to so that no one can connect to your network:
- Set a complex password on Wi-Fi.
- Put a complex password on the panel of the router itself.
- When paranoid - enable MAC address filtering, allow only for their devices.
- Turn off WPS (sometimes called QSS).
Phone hacking
All the methods above were mainly about using PCs. Kali Linux still remains the best environment for hacking - everything is already there. The ultimate option is Windows. With phones it is much more difficult. While preparing the article, I read “neighboring publications” with recommendations to stick Cali on Apple, or launch free Aircrack-ng on them right on Android or iOS, and a bonus with seasoning strange keywords - in short, this is not the case in life. If you want to break - put Kali, if there is only a phone - there will be no cool solution.
Basically, all the recommendations from the network on this field are frankly nonsense. My recommendation is to enter something like “wi-fi hacking” into Google Play or the App store, and you will get a whole selection of programs. And there already look at the reviews and do not put any fake rubbish. The main categories of software here:
- WPS password selection by default.
- Base points.
There will be no selection here - it requires computational power, which the phones (and some computers) do not have. So again - you want to break from the phone, put the potassium on a laptop / computer. On some smartphone models, Kali is installed, but if you are not a pro, don't even try - a meaningless undertaking.
A responsibility
Many people write about responsibility for a number of articles of the Criminal Code of the Russian Federation: 272, 273, 274. Even in high school they studied this question and somehow, then it all looked suspicious. Here are the titles of the articles:
- 272 - Wrongful access to computer information
- 273 - Creation, use and distribution of malicious computer programs.
274 - Violation of the rules for the operation of the means of storing, processing or transmitting computer information and information and telecommunication network
In fact, only 272 remains here. But let's look at it in more detail:
Unauthorized access to legally protected computer information if this act resulted in the destruction, blocking, modification or copying of computer information.
Please note that the use of the Internet itself, if this has not caused any damage, to put it mildly, it is difficult to adjust here. Another thing is if traffic or time is charged, and you use it ... But nowadays there is no limit on Wi-Fi around. No matter how it was there, I still categorically do not approve of any evil deeds in close surroundings - after all, we are all brothers, who if not us.
Programs
Powerful programs for hacking for all occasions really a bit. I recommend to pay attention to the following:
- Windows - WiFi Crack
- Kali Linux - Aircrack and Company. This is the best Wi-Fi cracker, most of the manuals from YouTube are about it, including the video from this article, it supports absolutely all ways of hacking, you can safely write a separate article. Ideal to work with a laptop, but you can also from a computer using Wi-Fi adapters.
- Android and iOS - discussed above, look in the markets, for me this is a “pseudo-cracker” in case of “what if you're lucky”.

